Remoteler replaces the #1 source of data breaches — secrets — with true identity to deliver phishing-proof zero trust access for every engineer and service connected to your global infrastructure.





Remoteler was designed to provide access to the infrastructure you need without slowing you down. With a single tool, engineers and security professionals get unified access to Linux and Windows servers, Kubernetes clusters, databases and DevOps applications like CI/CD, version control, and monitoring dashboards across all environments.

Secrets like passwords, keys, tokens, even browser cookies are the #1 source of data breaches. Any access solution that tries to make secrets more secure is just pushing back the inevitable.
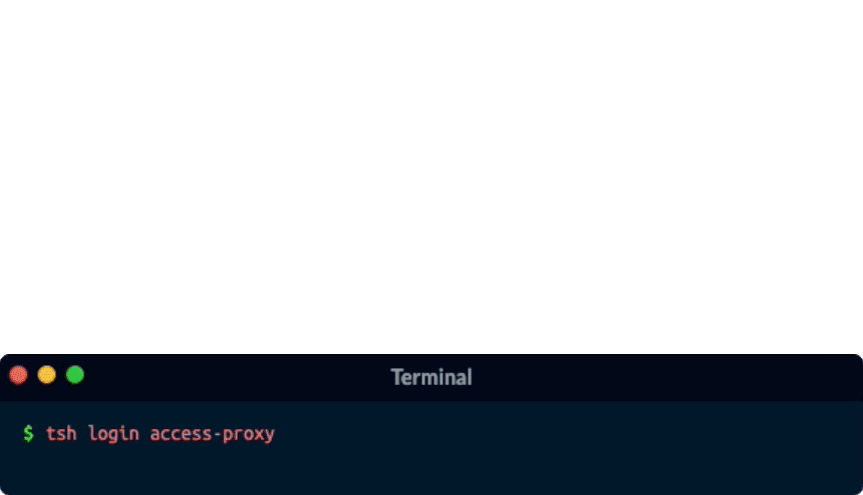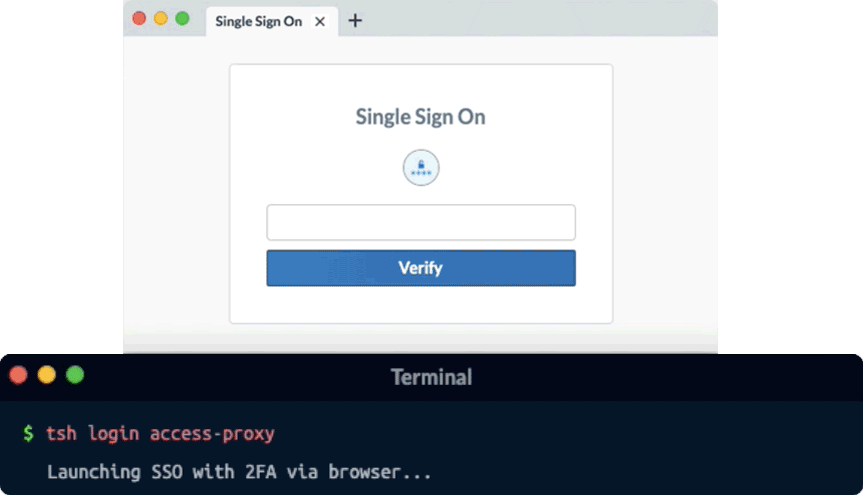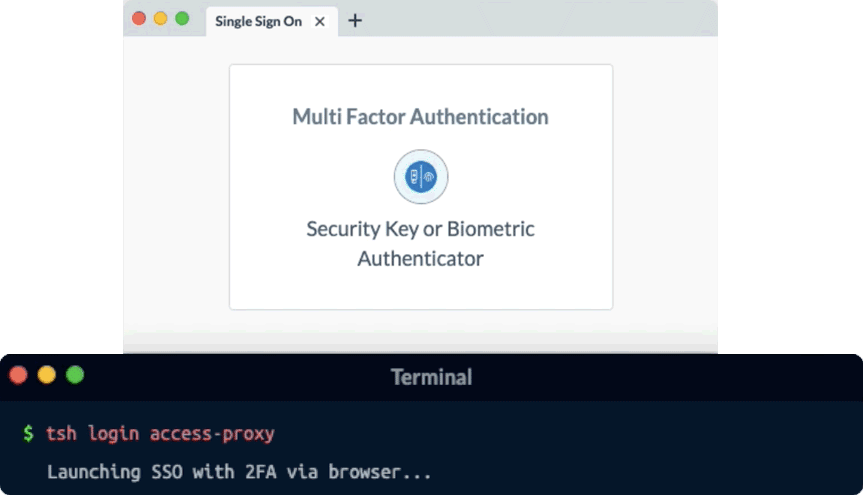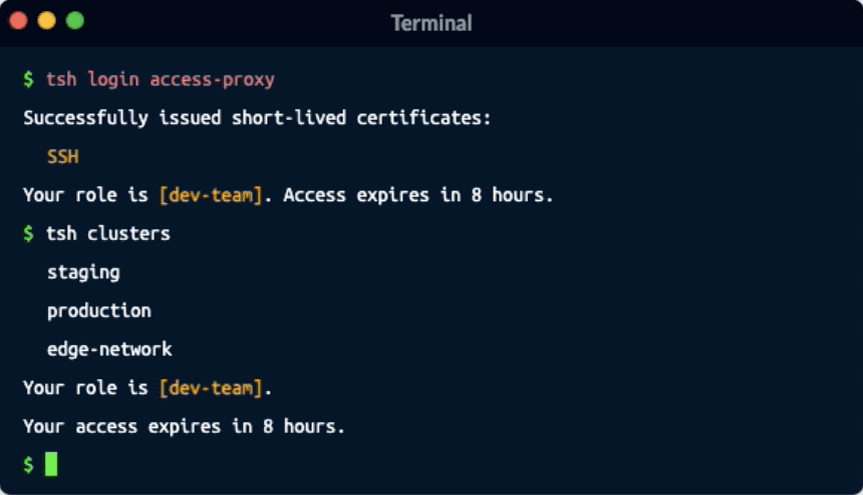
Remoteler’s Identity-Native access is different. By removing secrets from your infrastructure, phishing and pivot attacks are rendered useless since there is nothing to steal. Additionally, identity dramatically improves the access experience of engineers. Instead of juggling hundreds of credentials, all engineers need to do is login to Remoteler one time using secure biometrics.
This is why Remoteler is the one solution that engineering and security teams can agree on.
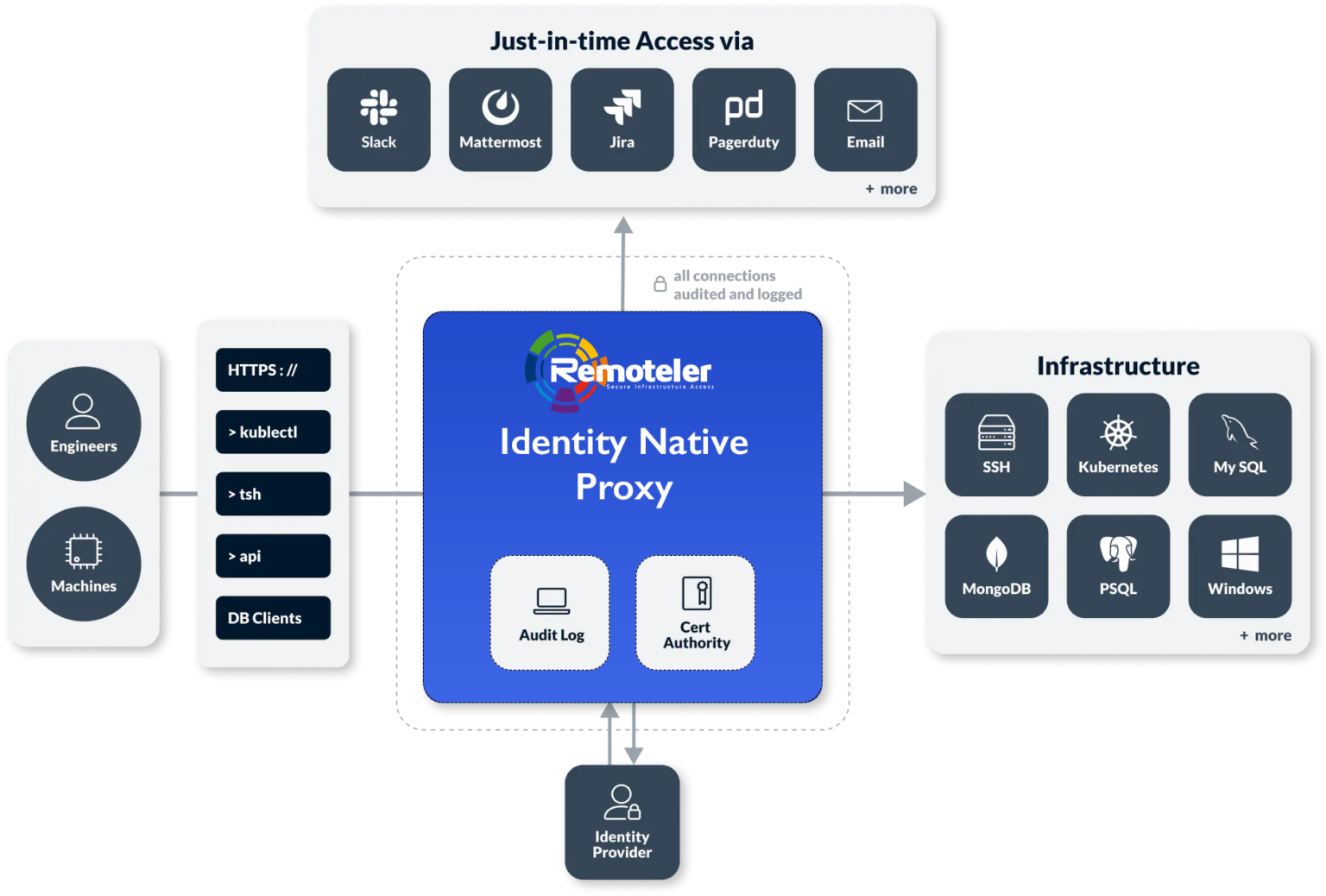
Remoteler’s unique architecture enables the secretless and zero-trust experience that both engineers and security teams love. Remoteler’s Identity-Native Access Proxy requires only a single open port to provide access to any Linux or Windows server, Kubernetes Cluster, Database or internal application.
With an optional lightweight Remoteler agent running on every host, you get dramatically deeper and more granular access controls and audit than VPN or homegrown bastion services can provide.
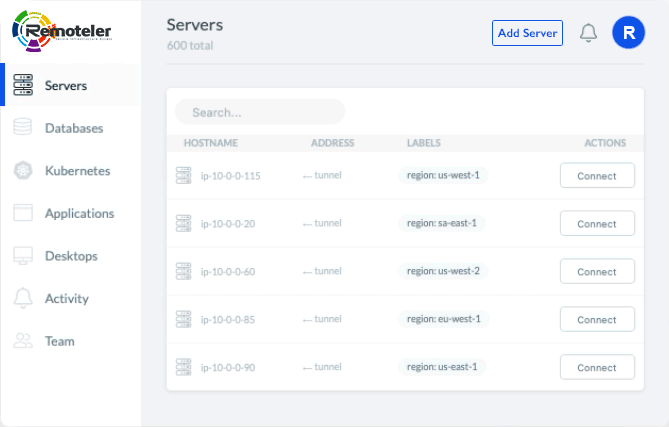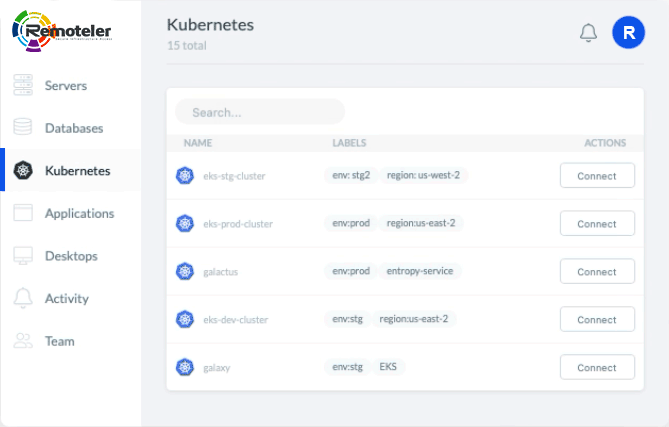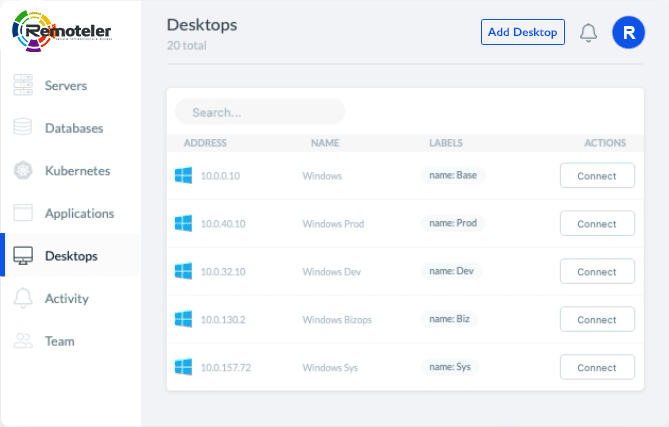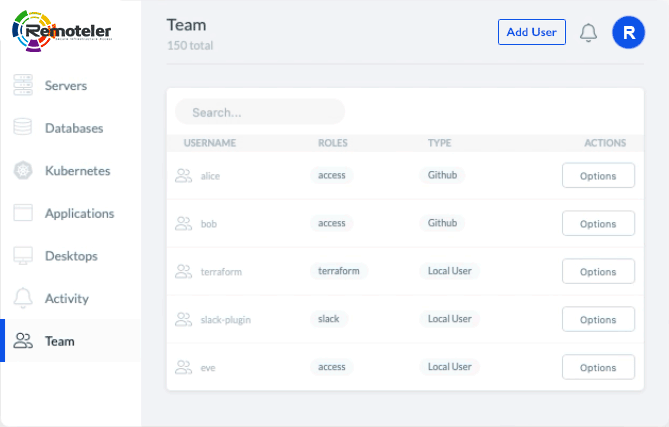
Consolidate identity-native access to SSH, Kubernetes, Databases, Applications, and Windows across your infrastructure.

Access any Windows host via the browser

SSH securely into Linux servers

Access your DevOps tools, monitoring, AWS Console

Access to SQL, NoSQL, and cloud databases

Access Kubernetes clusters securely
Remoteler Server Access is open source and relies on open standards such as X.509 certificates, HTTPS, SAML, OpenID connect and others. Deployed as a single binary, it seamlessly integrates with the rest of your stack.
