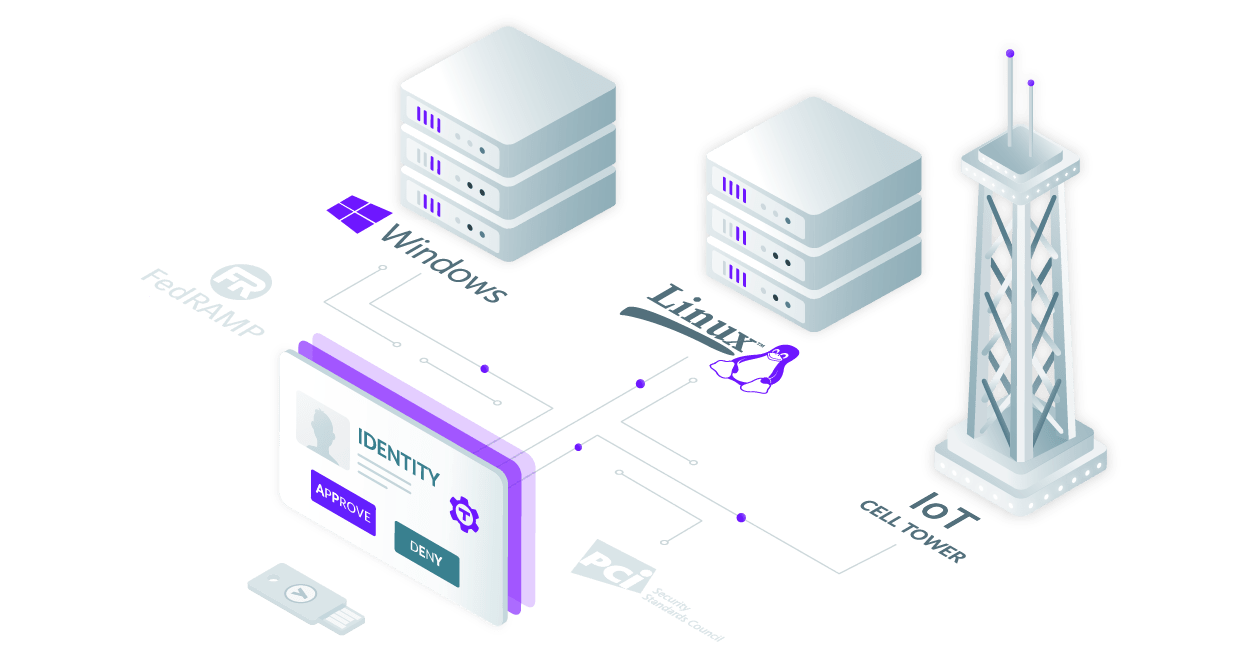
Consolidate identity-based server access across all environments, meet compliance requirements, and have complete visibility into access and behavior.
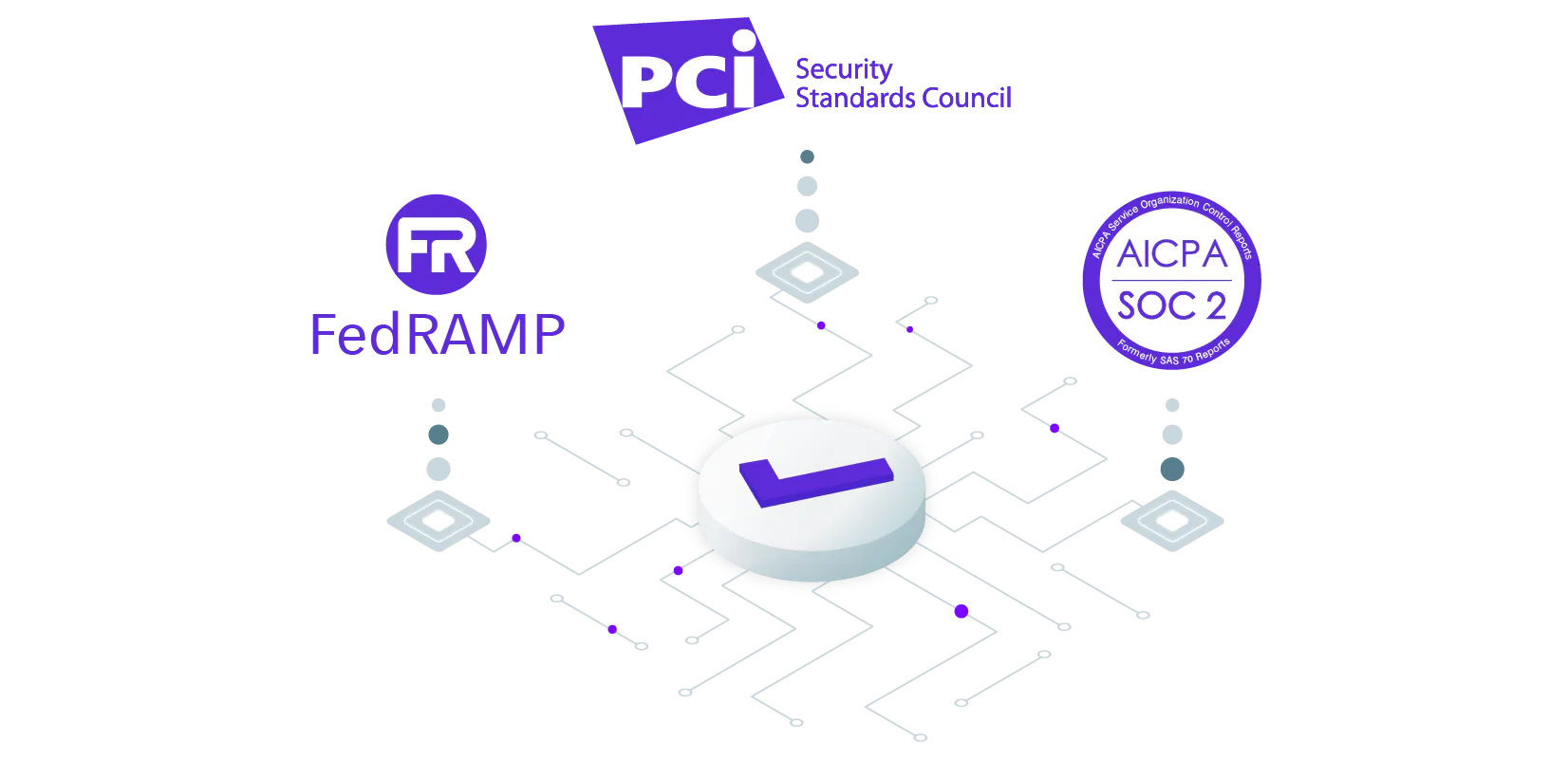
Remoteler was designed to continuously maintain compliance and pass audits with minimal configuration. The supported standards include SOC 2, FedRAMP, HIPAA, ISO 27001, PCI and more.
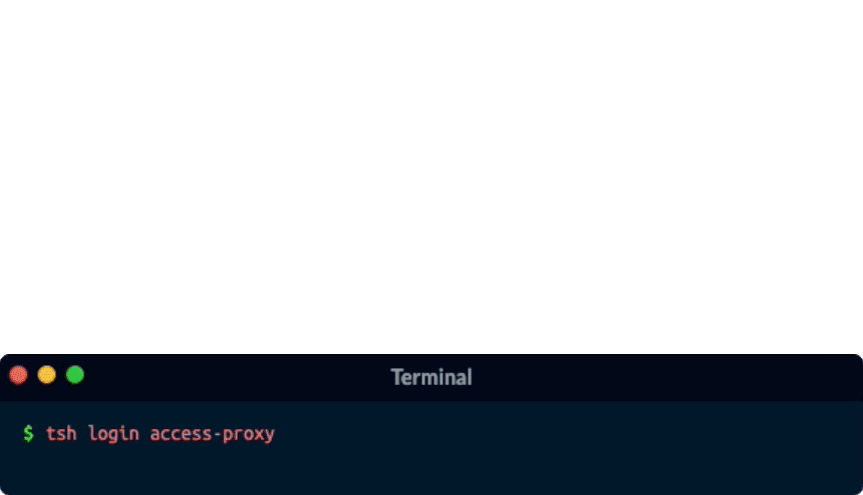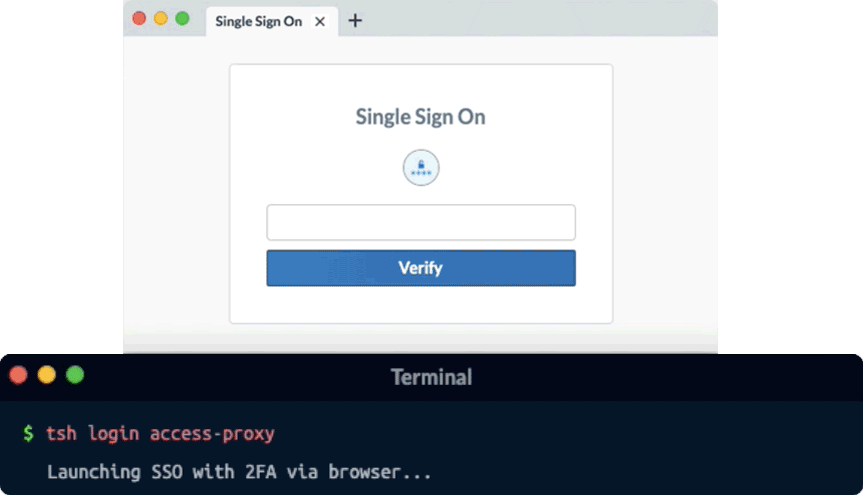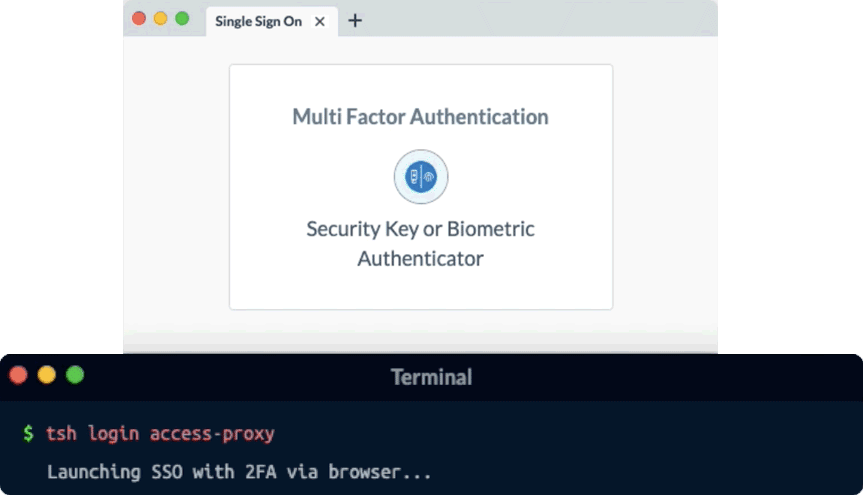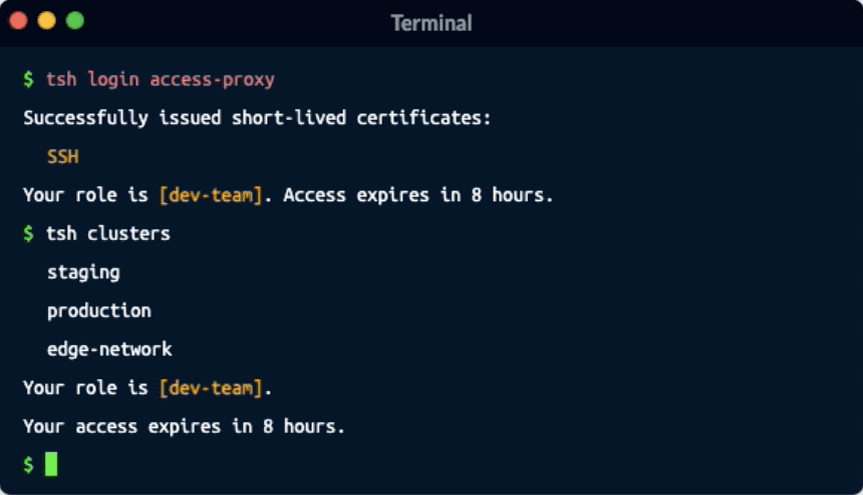
Designed for cloud-native workloads across multiple environments, Remoteler works with existing CI/CD solutions, in a terminal, and in a browser. SSH permissions are always in sync with other layers of your stack removing the need to juggle shared secrets, or hop between VPNs and multiple access points.

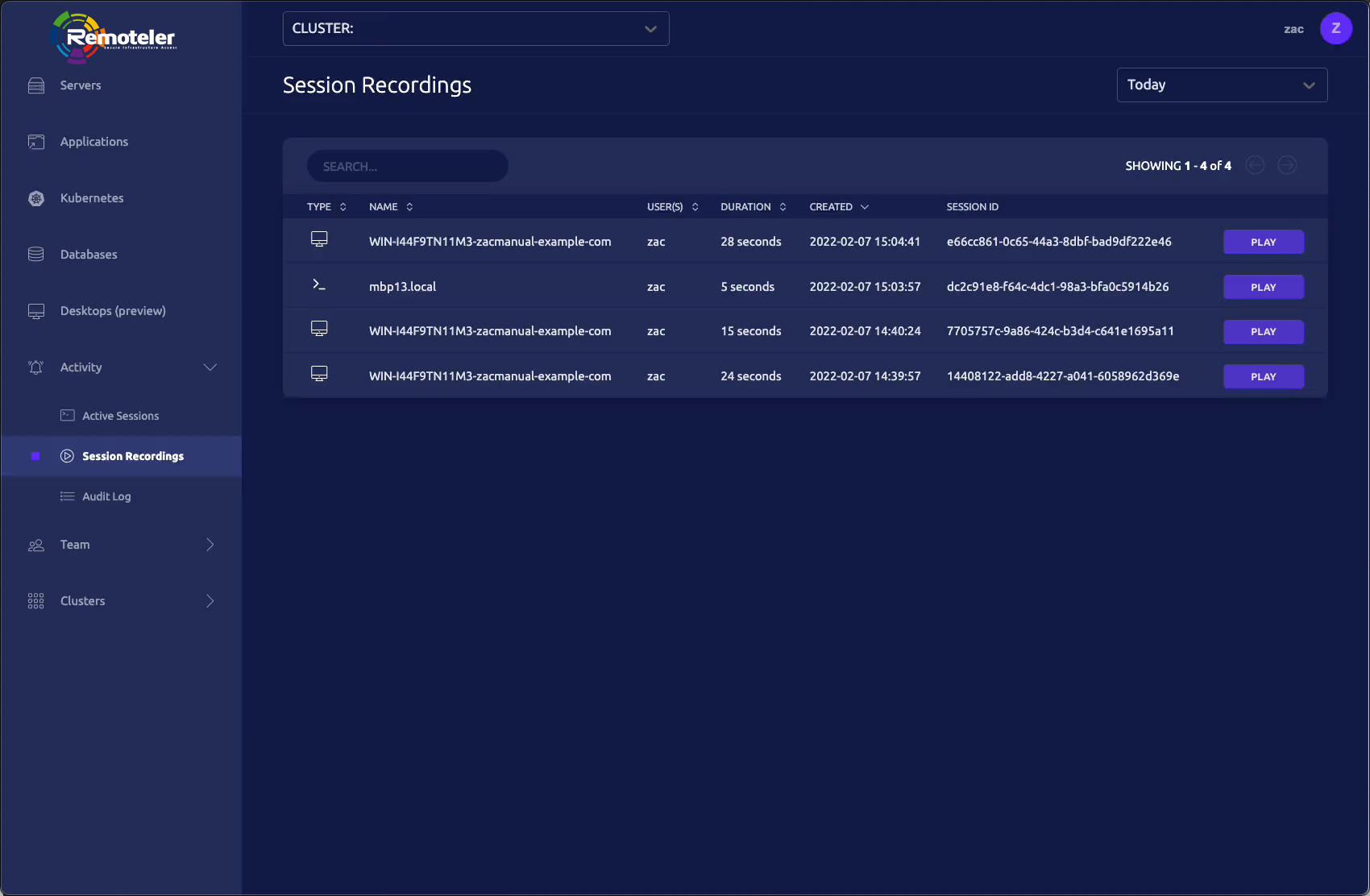
Remoteler provides a live view and an audit log for Windows user sessions across all environments, making it easy to see what’s happening and who is responsible.
Machine ID dramatically simplifies secure machine-to-machine access via SSH and X.509 certificates with access controls and audit built in.
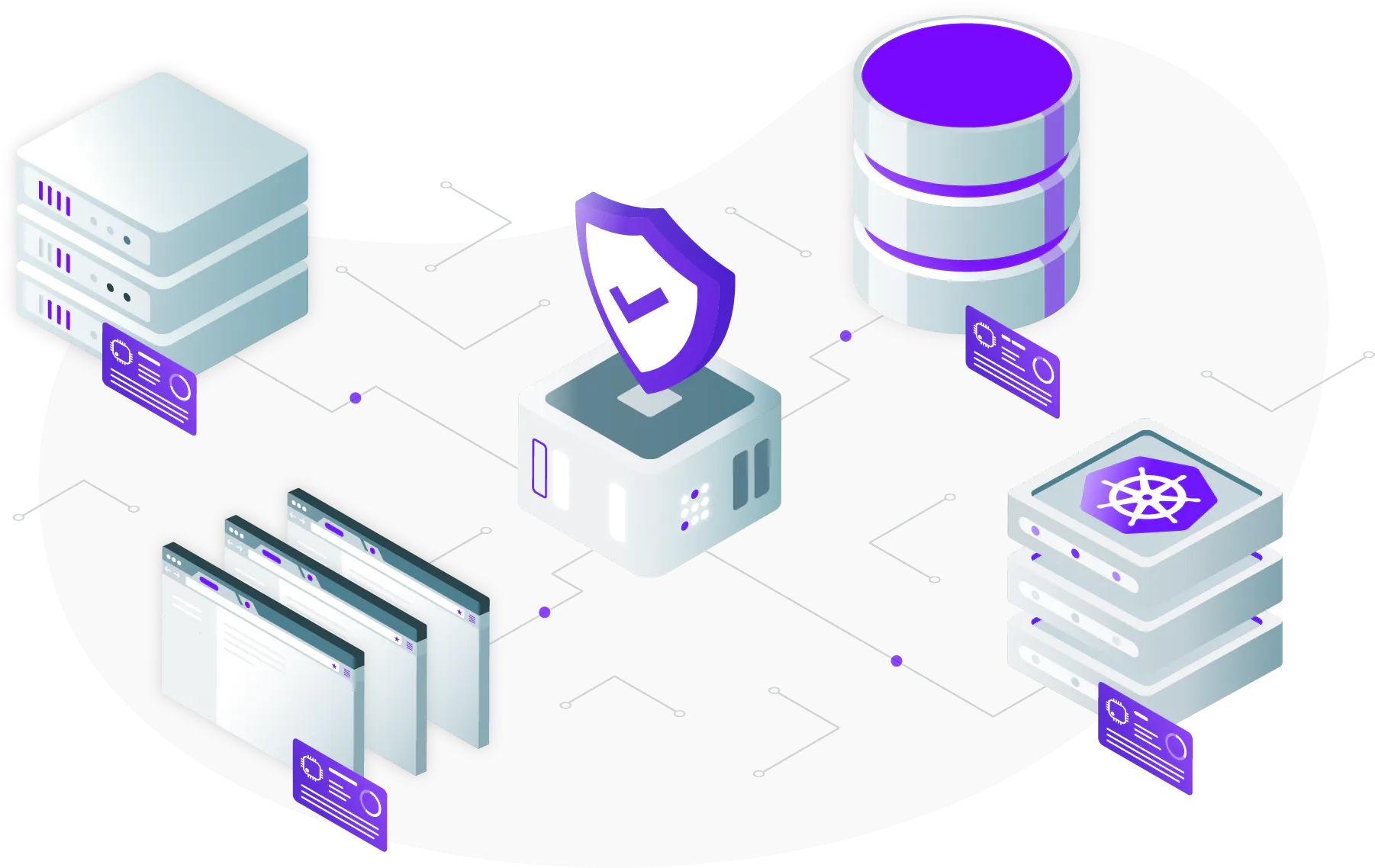
Remoteler Server Access relies on open standards such as X.509 certificates, HTTPS, SAML, OpenID connect and others. Deployed as a single binary, it seamlessly integrates with the rest of your stack and is fully compatible with OpenSSH and other SSH-based tooling.
