
Redis is an in-memory data store that stores data in key-value pairs. It’s primarily used as a cache for quick data access, as a database, and as a message broker.
Redis doesn’t have a default authentication setup in place exposing it to security vulnerabilities, which if exploited could potentially affect the infrastructure of the entire organization. These security vulnerabilities are what make securing your Redis database so important.
This article takes you through the steps and procedures for securing your Redis database using standard practices.
This section expands on the use cases that highlight the importance of securing your database. Due to a low-security setup by default, your data is accessible to hackers over the internet. This section looks at some reasons why securing your Redis database is important, including low-security defaults, personally identifiable information (PII) in cache, and the fact it’s a common target for hackers.
Redis is a popular choice for in-memory data storage, but it lacks built-in security features. The absence of a proper access control system allows unauthorized individuals to create non-encrypted passwords and altering of keys.
The cache can potentially hold your PII. This raises numerous security risks, leaving your data exposed to hackers and cybercriminals. Learn more about how having PII in cache can make your organization vulnerable.
Due to the widespread use of Redis, the number of attacks and threats to Redis databases has grown exponentially. Research by Imperva found that seventy-five percent of “open” Redis servers were infected with malware.
These are just some examples of why a multi-layer security posture is required for optimal functioning of your Redis database. There are multiple ways you can secure your Redis database, which are covered in the sections ahead.
This section covers the details of securing your Redis data store on three levels: network, transport, and database. You’ll also read about some additional security standards and methods for securing the Redis database.
Network security ensures that only the trusted nodes connect to your database in the network. This section covers some of the methods for securing your Redis database on the network level, including iptables, UFW, protected mode, and setting up IP restrictions.
iptables
iptables is a firewall program that’s built for Linux and handles the monitoring of traffic in your network.
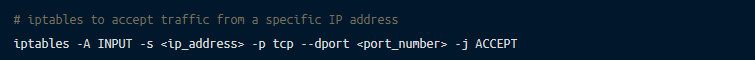
By default, the Redis database accepts the connections on port 6379. You can utilize iptables to accept traffic only from a specified IP address; this helps protect you from security threats.
Here’s how to use iptables:
Redis Protected Mode
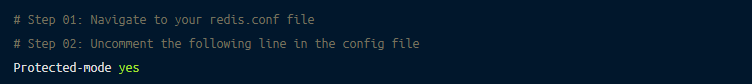
Whenever you’re using Redis in the cloud, it’s better to enable protected mode for enhanced security. Protected mode ensures that the database only responds to the loopback address and generates an error as a reply to all the nodes connecting from other IP addresses.
To enable protected mode, the steps are as follows:
IP Restrictions
Redis Enterprise Cloud provides two additional network security features: IP restrictions and virtual private clouds (VPCs). IP restrictions are almost the same as iptables.
To enable them, navigate to Admin Console > View Database. Click edit, then Access Control & Security. Turn on Source IP/Subnet and add the required IP addresses.
Similarly, you can set up VPCs in Redis Enterprise Cloud.
Transport-level security (TLS) ensures the encryption of data for secure transportation. You can set up the TLS-enabled Redis cloud to protect your Redis database. This section covers the steps needed to set up the TLS cryptographic protocol, along with the authentication mechanism.
TLS-Enabled Redis Cloud
You can set up the TLS cryptographic protocol and client authentication in Redis Cloud. Client authentication requires clients to present an authentic client certificate before giving them access to resources.
First, you need to enable the TLS and client authentication. For that, navigate to Admin Console > Databases. Select your database and click edit. Go to Access Control & Security and enable SSL Client Authentication > Enforce client authentication. Provide the X.509 certificate or click Generate Client Certificate. The download will start. Next, click Update.
Once you’ve downloaded the certificates, you can connect to the Redis Cloud using the following command:
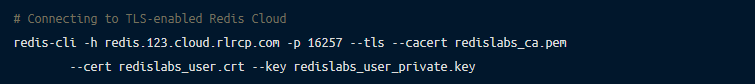
You can learn more about TLS-enabled Redis Cloud.
Database-level security defines the users’ roles and their privileges in the database. In this section, you’ll learn about the standard practices of securing your database, including giving access only to Redis users, running the Redis database as an unprivileged user, and setting up a stronger password to avoid unauthorized users accessing your Redis database.
Allowing Access Only to Redis Users
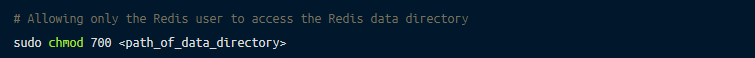
By default, the primary access to data folders lies with the Redis user and the secondary access with the Redis group. For improved security, it’s important to allow only Redis users access to the Redis data directory.
You can use the following command to ensure that access is limited to Redis users:
Running the Redis Database as an Unprivileged User
There are high security risks associated with running your Redis database as the root user, because if a cybercriminal hacks a session where the root user is active, all the permissions to alter data will be granted.
Therefore, to protect the database from security risks, it’s recommended that you run your Redis database as an unprivileged user, which is a user with restricted permissions.
Setting Up a Stronger Password
You can also secure your Redis database by setting up a stronger password instead of the default one. The change of password needs to be made in the redis.conf file, using the following steps:
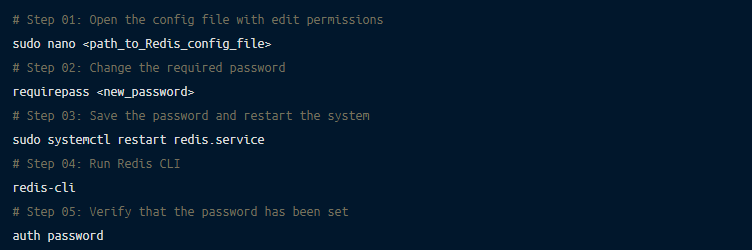
Learn more about making a secure password for Redis.
By default, there’s no authentication system in the Redis database. Therefore, the AUTH command is utilized to set up authentication so that only trusted users can access the server.
The server compares the password entered during the time of connection, and if it matches with the one in the config file, it accepts the commands from the node. You can set up the AUTH command with the following steps:
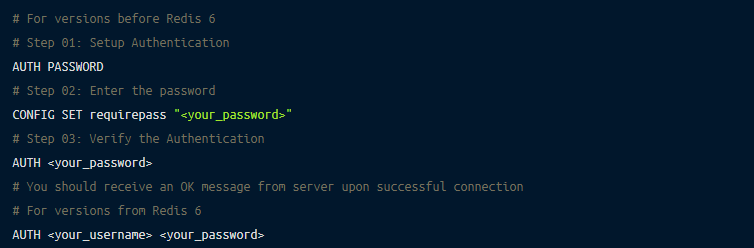
You can read more about the AUTH command.
There are some common commands in the Redis database that could be dangerous if executed by an unauthorized user. For example, a single FLUSHALL command can erase all your data.
To avoid misuse and enhance security, you can rename these commands.
The following are the steps for renaming common commands:
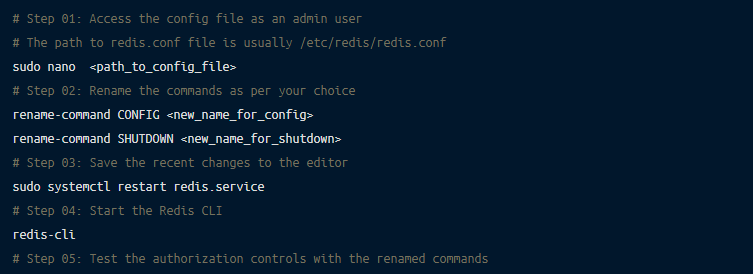
The previous section covered the details of renaming the common commands. However, you can also disable the vulnerable commands by setting them to empty strings. The syntax is as follows:
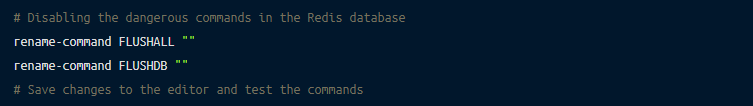
Your Redis database allows you to set user permissions and access, which can make your setup more secure. For this purpose, the ACL command is utilized.
The following is the generic command to achieve this:
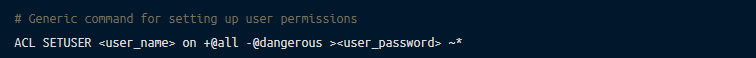
The above command allows all permissions to the user and then removes all commands tagged as dangerous.
There’s a whole list of permissions offered by the Redis database; you can learn more about the command categories in the Redis documentation.
The following is an example of setting user permissions:
# List the default permissions of the user
ACL LIST
# Allow the permissions to the user (The user has a password and can access key names starting with ‘cached’ using the GET command )
ACL SETUSER <username> on > <password> ~cached:* +getYou can also find out how to create a user and allot them permissions using the ACL command.
Your Redis database provides distinct encryption at rest options based on deployment method. We’ll review three of these: Google Cloud Platform (GCP), Microsoft Azure, and AWS.
Encryption at Rest in Google Cloud Platform
All the data in the Redis database in GCP is encrypted by default. Therefore, no additional steps or methods are required for enabling the encryption at rest. Navigate to encryption at rest in Google Cloud to learn more about it.
Encryption at Rest in Microsoft Azure
Similar to GCP, the data in Redis Cloud deployed on Microsoft Azure is encrypted at rest by default. Navigate to encryption at rest in Azure to learn more about it.
Encryption at Rest in AWS
You can set up encryption at rest in AWS when creating flexible plans. For that, the steps are:
Create a new AWS subscription by clicking Create under the Flexible plan option. Once the subscription is created, click on Advanced Options and enable Set Persistent Storage Encryption.
To find out more, navigate to encryption at rest on AWS.
You can set up multifactor authentication (MFA) in Redis Enterprise Cloud. You’ll need your username, password, and an authentication code to access the account.
The steps for the setup of MFA are: Log in to your Redis Enterprise Cloud account. Click Name > User Profile > Multi-Factor Authentication > Activate Now. Enter the mobile number and confirm the code by verification message.
You can learn more about Redis and multifactor authentication.
In this article we looked into numerous methods of securing your Redis database. However, you can significantly simplify the process of securing your databases using Remoteler Database Access.
Remoteler brings together the authentication, authorization, auditing, and connectivity of cloud applications in one place. With Remoteler, you don’t need to worry about security practices, as it handles the complete security of the tech stack by default.
You can find out more in this Remoteler introductory video, through GitHub code, and in the documentation about securing your self-hosted Redis database using Remoteler Database Access or if securing a Redis Cluster.
Redis is a popular choice as a database, cache, and message broker. However, its default security settings are leave the database quite vulnerable. In this article, we covered numerous methods of hardening the Redis database on three levels: network, transport, and database.
We also looked into the additional security procedures like the AUTH feature, renaming of common commands, managing user permissions, encryption options, and multifactor authentication.
You can simplify the process of securing your Redis database by utilizing Remoteler, which is an identity-aware and multi-protocol proxy, bringing together all the aspects of securing database access in one platform.